Introduction
Introduction
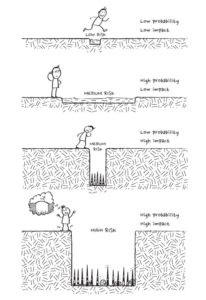
I believe complexity is the enemy of execution and unnecessary complication is often tied to ego and lack of clarity. In cybersecurity just about everything is overly complicated. I’m not sure why. I sometimes even wonder if I understand cybersecurity. With all the frameworks, best practices, maturity models, team/hacker colors, next-gen appliances, etc., it’s hard to keep up. The cybersecurity industry seems to want to learn new methods to slam dunk, without learning how to dribble first. I get it – slam dunking is sexy; dribbling is boring. The fact of the matter though is most people that master a skill get very good at a few key moves and ignore the rest.
In cybersecurity, there’s this notion that you need to master 100 things to be secure. This doesn’t work. The reality is mastering the Top 5 to 6 things is often enough, especially if you know your critical assets (data and systems) and the risk facing them.
Risk – Traditional Definition
Risk is a misunderstood and elusive topic in cybersecurity. Over my career I’ve met very few cybersecurity professionals that actually understand risk. Sure, they read about it in a book or learn about it preparing for the CISSP or Security+ certification exams, but they don’t really understand risk. They’ll tell you the formula:
Risk = Threat X Vulnerability
This is what the academics say. What does this really mean though?
What is a threat? What is a vulnerability?
What about impact or probability? These aren’t even listed in the equation above, yet they are the most important parts.
A threat is something that could cause damage.
A vulnerability is an exposure to a threat.

So, using the formula that most cybersecurity professionals have been taught for risk, it’s understandable why it’s not understood.
If a threat is water from rain and the vulnerability is an open car window, what’s the risk?
Risk = Water X Open Car Window ?
This is where most cybersecurity professionals start mumbling about frameworks, qualitative, quantitative, and other lingo with the intent to complicate something that should be simple. And, there’s not much you can do with that formula – very little value.
The problem is how do you prioritize which open car windows to close first? If you are a nationwide organization with 1000 cars and 800 of them have an open window, what do you do? You only have so many resources.
Let’s dig a little deeper on this.
Of the 800 cars with open windows, they fall in different categories:
Arizona
- 50 brand new cars parked in garages
- 50 brand new cars parked outside
- 200 old cars parked in garages
- 100 old cars parked outside
Seattle
- 50 brand new cars parked in garages
- 50 brand new cars parked outside
- 200 old cars parked in garages
- 100 old cars parked outside
So, using the risk formula, what do you do? Risk = Threat X Vulnerability
Exactly. The formula is kind of useless. You can’t close all the car windows at once – you have limited resources.
Risk – Practical Explanation
A more useful risk formula is Risk = Probability X Impact
Risk = Probability of Threat Being Realized X Impact if Threat is Realized
Probability can also be referenced as likelihood.
Impact can also be referenced as a consequence.
To me, this makes more sense than Threat X Vulnerability, which is what CISSP and other cybersecurity certs teach us.
Let’s take the open car window scenario:
Arizona
- 50 brand new cars parked in garages
- 50 brand new cars parked outside
- 200 old cars parked in garages
- 100 old cars parked outside
Seattle
- 50 brand new cars parked in garages
- 50 brand new cars parked outside
- 200 old cars parked in garages
- 100 old cars parked outside
Likelihood of rain (water)
- Seattle = Near Certain
- Arizona = Likely
- In Garage (location doesn’t matter) = Rare
Impact:
- New car = Significant
- Old car = Minor
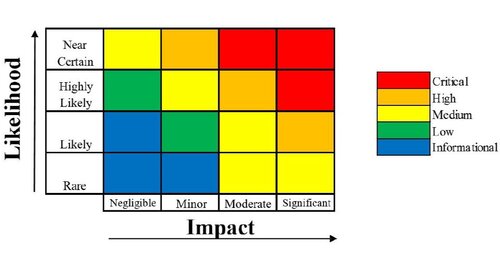
Which windows do we close first? Let’s use the matrix as a guide.
-
Seattle, New Car
-
Seattle, Old Car
-
Near Certain X Minor = High Risk
-
-
Arizona, New Car
-
Likely X Significant = Medium
-
-
Arizona, Old Car
-
Likely X Minor = Low
-
-
Garage, New Car
-
Rare X Significant = Medium
-
-
Garage, Old Car
-
Rare X minor = Informational
-
So, we would prioritize the windows to close in order of risk:
- Critical Risk = Seattle, New Car
- High Risk = Seattle, Old Car
- Medium Risk = Arizona, New Car
- Medium Risk = Garage, New Car
- Low Risk = Arizona, Old Car
- Informational Risk = Garage, Old Car
Conclusion
Think of risk in terms of probability and impact, not threat times vulnerability.