 A foundation of cybersecurity is, where is the risk? Based on risk comprehension, professionals map out a cybersecurity framework and strategy. While risk assessment is essential to executing proactive and reactive cybersecurity plans, the gap is that a deep understanding of risk is not as widespread as you’d imagine.
A foundation of cybersecurity is, where is the risk? Based on risk comprehension, professionals map out a cybersecurity framework and strategy. While risk assessment is essential to executing proactive and reactive cybersecurity plans, the gap is that a deep understanding of risk is not as widespread as you’d imagine.
The reality is that risk comprehension is a basic cybersecurity skill, yet most practitioners lack it. In this post, we’ll be breaking down:
- What is risk comprehension?
- Why is there a gap in professional proficiency in the area?
- How to ensure professionals gain this expertise and know how to execute it in cybersecurity operations.
What Is Risk Comprehension?
Simply put, it’s having a full technical understanding of risk fundamentals within the cybersecurity ecosystem. Beyond just the confines of cybersecurity, life is about risk, in general. So, the inability to grasp it in cybersecurity directly relates to the bigger picture of people not comprehending risk.
Quantifying Risk
In most areas of certification or academic, risk is a formula:
Risk = Threat x Vulnerability
In unpacking this formula, you can see it’s easy for it to be confusing. How are threats and vulnerabilities quantifiable?
In my book, The Smartest Person in the Room, I describe a more palatable formula:
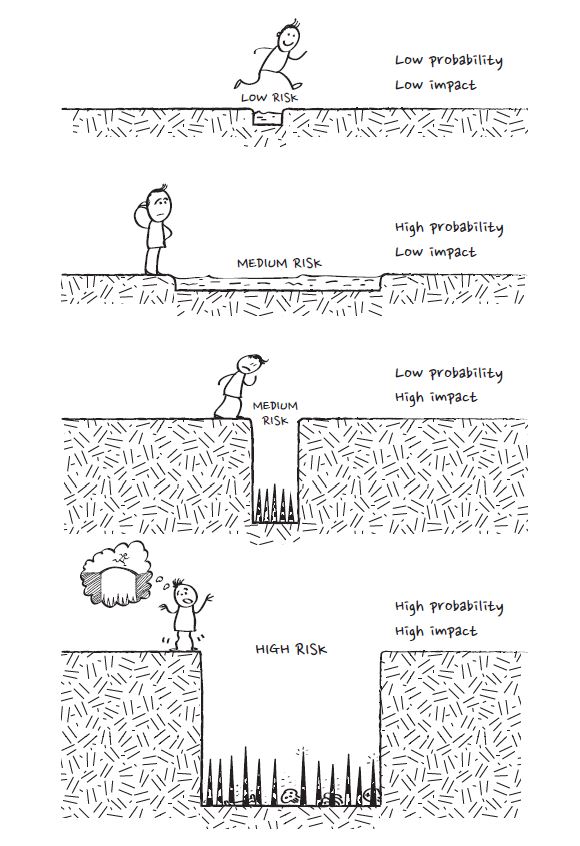
Risk = Probability x Impact
In other words, how likely is something to happen, and what’s the consequence if it does?
The answer to this formula will identify three kinds of risk:
- Low risk has a low probability and impact.
- Medium risk could have high probability and low impact or low probability and high impact.
- High risk is highly probable and impactful.
Cybersecurity Risk Is Just Another Operational Risk
The risk of cybersecurity incidents falls into the broader category of operational risk. The types of risk include those that could involve:
- Financials
- Reputation
- Operations
- Productivity
- Accessibility
- Regulatory
- Damage to equipment or hardware
With many opportunities for impact in this area of risk, hackers can seize on vulnerabilities. Further, cybercriminals will take advantage of risk indecision. Thus, it’s imperative to have risk literate cybersecurity professionals.
Why Cybersecurity Professionals Need to Grasp Risk
The concept of a cybersecurity professional is one that mitigates risk and secures data. It’s the two-second job description. Knowing, you’d think these people would be risk experts. Yet based on my experience running a cybersecurity firm and teaching cybersecurity to college students, I can tell you there’s a gap.
This lack of understanding risk is complicating the industry. It should be a simple connection that will enable cybersecurity professionals to do the best job. Instead, we’re seeing an influx of paper tigers in the industry. These are the folks with cybersecurity certifications on their resume. They look ideal on paper, but when hired, are immediately like a fish out of water. They don’t have the necessary skills to fall back on, so they begin a routine of destructive behaviors affecting your company and their ability to succeed.
You’ll find those who don’t have this risk knowledge to begin posturing to cover this deficit. Posturing is a defensive response that involves overcomplicating processes and a pursuit by the professional to always be right and the smartest person in the room.
While professionals are busy doing this, hackers are seeking out ways to find vulnerabilities and exploit them.
Shifting to a Risk-Based Approach to Cybersecurity
In talking about cyber risk, there has been a migration from maturity-based to risk-based. To successfully change to this approach, cybersecurity teams need to improve risk comprehension.
The model is dependent upon identifying and focusing on the most probable and high impact risks. Doing this requires a full understanding of the threat landscape and the ability to prioritize them.
What Is Maturity-Based?
The traditional maturity-based approach focused on a level of maturity for capabilities in the realm. The goal was to reach maturity in assessing, monitoring, and reacting to potential risks. Additionally, the model used access controls like two-factor authentication. Maturity-based isn’t completely obsolete. It can be a good jumping-off point for building a cybersecurity program.
However, most organizations are past this step. The maturity-based method has unfortunately led to unmanageable scaling. Will you monitor everything? Can you? Spending becomes out of control for this approach, as well.
The most limiting part of such a model is it can paralyze implementation efforts. However, many professionals in the field will promote and follow maturity-based methods over risk-based. Why? You don’t have to understand risk to pull it off.
What Is Risk-Based?
The key elements of being risk-based include:
- Full comprehension of cyber risk
- Prioritization of risks based on probability and impact
- Measuring security controls to understand your performance against risk
- Inclusion of all stakeholders in the cybersecurity space
The objective of risk-based is to make risk reduction an outcome. Organizations must focus on the right controls, processes, skillsets, and investment to reach these outcomes. Before you can achieve a risk-based approach, you have to excel at all the elements. Number one is risk comprehension.
Improving Risk Comprehension for Cybersecurity Professionals
The first question that comes up is why don’t professionals have this skillset? Didn’t they learn about it during training? It must have been a question on the certification?
Next, we’ll look at why risk comprehension is lacking and how to improve it.
Better Training
Educational courses obviously talk about risk, but many just teach the student to score well enough on a multiple-choice test. Thus, they simply have to memorize answers, and they pass.
Hands-on, real-world training is much more than choosing the right letter. They prepare individuals more holistically to succeed in the field. If you want your team of cybersecurity professionals to operate in a risk-based scheme, then you need to ensure they know what it is! Look for candidates with training from organizations recognized for being more than a certification mill.
If your current team lacks this knowledge, then find ways to upskill them so they can grasp the concept. If they posture and affirm they don’t need it, they might not be the best fit. They must admit they don’t know everything and change their mindset. Not all are capable of this.
Embracing a Growth Mindset
Fixed mindsets aren’t going to get your organization to a better risk posture. Those with fixed mindsets aren’t open to change or evolution, whereas a growth mindset is. Associated with this mindset are soft skills. They are much harder to learn and adopt as habits than hard skills. Professionals must have the desire to adapt, which will include working on communication and collaboration efforts.
Keep in mind that communication is more than what you say. What matters most is the tone you use and your body language. While some may be eloquent or articulate, that doesn’t mean they have great communication skills. The most important communication adjustments are asking the right questions about risk and really listening to the answers from all stakeholders. You have to think about it from a technical and business side.
Tempering Change with Acknowledgement
If you’re a technology leader and want people to improve their skillsets, it’s good to acknowledge what they are doing well. When you do this, people will be more open to the next part of the conversation.
As your team evolves to become risk-based and practices soft skills, keep acknowledging them to keep them motivated.
Rewiring for Monotasking
We think that multi-tasking illustrates great productivity and time management. In cybersecurity, multi-tasking can cause errors and distractions. Monotasking helps keep the focus on quality. It may take longer to get certain things completed, but it also means that you’re less likely to have to redo something or be open to more significant threats because of mistakes.
Cultivating Connection with Empathy
Empathy is probably the greatest attribute anyone could have in any situation. Cybersecurity professionals who possess compassion are better leaders and better at risk comprehension. They can communicate and collaborate better. They also think outside small boxes of “what is risk?”
Helping individuals become more empathetic has lots of consequences beyond being better at risk.
Building Better Cybersecurity Teams
Many of the things discussed are part of my Secure Methodology, which is part of my book, The Smartest Person in the Room. I’ve devised a seven-step process to improve cybersecurity professional skills and thus boost risk-based methodologies. It’s a unique approach that builds on fundamentals.
Learn all about it by ordering the book today!












