 This blog post is a transcript of Christian Espinosa’s explanation of the Cybersecurity CIA Triad, and the opposite – DAD, and covers the following:
This blog post is a transcript of Christian Espinosa’s explanation of the Cybersecurity CIA Triad, and the opposite – DAD, and covers the following:
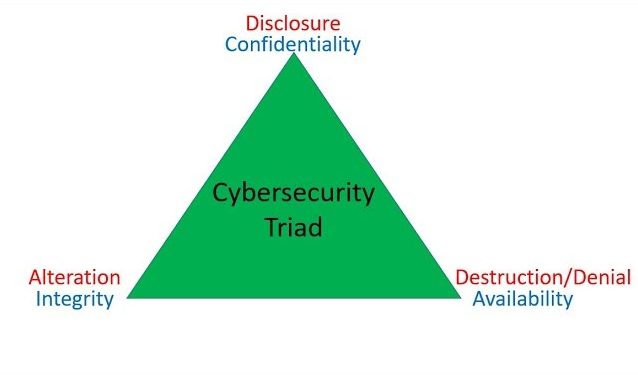
- CIA = Confidentiality, Integrity, and Availability
- Technologies used for each:
- Confidentiality = Encryption
- Integrity = Hashing
- Availability = Load-Balancers, Hot Sites
- DAD = Disclosure, Alteration, and Destruction/Denial
Check out my latest book: https://christianespinosa.com/books/the-smartest-person-in-the-room/
In Dec 2020, Alpine Security was acquired by Cerberus Sentinel (https://www.cerberussentinel.com/)
Need cybersecurity help? Connect with me: https://christianespinosa.com/cerberus-sentinel/
Complete Cybersecurity CIA Triad Explanation Video Transcript
Hey everybody. This is Christian Espinosa with Alpine Security. Today’s topic is on CIA, not the Central Intelligence Agency, but confidentiality, integrity and availability. These three things are what we try to achieve with cybersecurity.
With confidentiality, we’re trying to prevent unauthorized disclosure of our data. The technology we typically use with confidentiality is encryption. So I want to encrypt my data in transit and at rest. So if I’m sending some data to Amazon, such as my credit card number, and somebody intercepts it, they can’t read the data unless they have the encryption key. It’s kept secret. If somebody steals my hard drive and I’ve encrypted my hard drive, my data is not disclosed to them unless they can decrypt the hard drive. So confidentiality, the technology we use is encryption.
Integrity is to make sure our data is not altered, either intentionally or unintentionally. That technology we use for integrity is hashing. So if we use a hashing algorithm, such as MD5, SHA1, SHA512, if we use any of those, we take the data, we run it through this hash algorithm, it spits out what’s called the message digest, that if I send you the data, you run the data you received from me through the same hash algorithm, you get a message digest. If your message digest matches, sorry, my message digest, then the data has not been altered. So that’s hashing and that’s used to prevent alteration or to see if data has been altered.
The a stands for availability. If the data is not available, it’s kind of useless. With availability, we typically use things like load balancers, backup sites, hot sites, mirrored sites, et cetera for availability.
The opposite of CIA, is DAD. That stands for disclosure, alteration and destruction. With disclosure, it’s the opposite of confidentiality. So if your data is disclose to me or to a hacker, you have no longer achieved the objective of confidentiality. With the A, alteration, if your data is supposed to have integrity, but I’m able to alter it. Let’s say I go to your shopping cart and I can change the price of your thousand dollar item to $1 then I’ve altered your data and that is not achieving integrity. The other D stands for destruction or denial of service. So if I’m able to destroy your system, like your server, or do it the of service on your server, then I have removed the availability of your system to your users. So that’s DAD, disclosure, alteration and destruction.
I hope you enjoyed this. Quick tutorial on CIA and DAD. If you have any questions or comments leave them beneath the video. Please subscribe to our channel. Thanks. I’ll talk to you later.


