 In the conversation regarding cyber threats, the perspective is typically on defeating cybercriminals. The threat lens is from the outside, which is very true. Hackers are motivated and persistent in their pursuit of stealing data, deploying ransomware, and causing havoc.
In the conversation regarding cyber threats, the perspective is typically on defeating cybercriminals. The threat lens is from the outside, which is very true. Hackers are motivated and persistent in their pursuit of stealing data, deploying ransomware, and causing havoc.
However, the cyber threat that’s as potent is what’s happening within an organization. A lack of a cybersecurity culture can increase risk exponentially. While the concept of a cybersecurity culture isn’t new, it’s still a challenge for most technical teams. When not present, cyber professionals work in siloes, avoid accountability, communicate ineffectively, and erode collaboration.
If these characteristics seem too familiar, it’s time to address, reimagine, or build a culture that values communication, collaboration, curiosity, awareness, and cooperation. Failure to pivot and adopt such a framework could be the reason that you become a cyber statistic.
What’s the Ideal Cybersecurity Culture?
For the purpose of this discussion, I’m referring to cybersecurity culture as the principles and values of the cyber team, not the enterprise. There is a difference. In the latter, cybersecurity culture describes all stakeholders and employees to understand the threat landscape and work toward adopting best practices to avoid things like phishing attacks.
In terms of your team, cybersecurity culture is the environment in which your technical folks work to prevent attacks, analyze risks, deploy new strategies, and keep the organization as secure as possible.
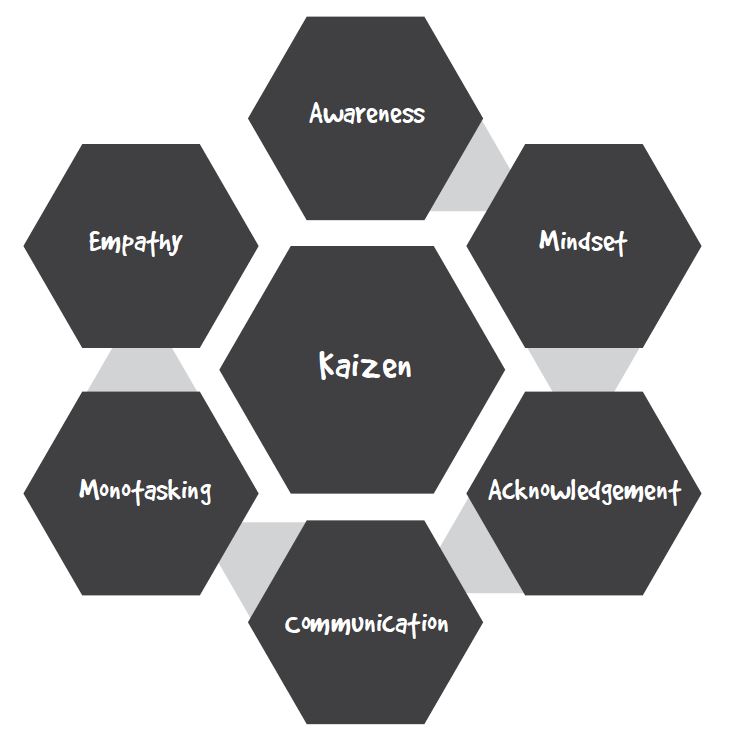
The ideal culture to aim for includes these ingredients:
- Consistent and clear communication
- Awareness around someone’s actions and the perspectives of others
- A foundation of trust and respect
- Collaborative interactions that support the organization
- Championing a growth mindset where individuals can adapt and evolve
- Empathy and understanding other’s feelings and perceptions
You may find this list overwhelming, but they are the tenets of any effective culture. Each of these elements is necessary to drive progress on the individual and team levels. So, what happens when culture is nonexistent? And what’s the impact of risk?
A Lack of Cybersecurity Culture Compounds Risk
As a cyber professional, your entire view of your actions is measured in risk. Even those businesses with robust cyber controls still have exposure to risk. It’s unavoidable in the modern age. Except that the threat isn’t always outside. Cybercriminals are rightly painted as the enemy, but the absence of a cybersecurity culture makes you more vulnerable. Here’s why.
Shared Responsibility and Accountability Failures
Your cyber team must be one that shares responsibility and takes accountability. There is no leeway on this one. It would seem to be a given that your people must work together in every component of security. Unfortunately, this isn’t happening in most organizations.
The reasons are complex, but ultimately, it comes down to the fact that technical folks have deficiencies in people skills. They are defensive and aggressive with communication and singularly focus on what they believe are the proper practices. Instead of forming a team to defeat the hackers, they often in-fight with one another, each trying to take the title of the smartest person in the room. As with any situation like this, internal animosity gives cybercriminals the edge.
Communication Stalls, Heightening Risk Incrementally
When your people are acting as teams of one, communication is toxic and ineffective. It comes out as snide remarks with an air of condensation in every word. How can a team protect your organization when they can’t even communicate?
You likely recognize the attributes of dysfunctional communication within your team. Although, you might not see it for the risk it truly is. Without a set of rules around discussion and conversation as part of your culture, you will experience greater risk in every area of cybersecurity.
Acknowledgment Gaps Grow Seeds of Disengagement
Another key part of a cybersecurity culture is acknowledgment. All too often, the only acknowledgment teams receive is about what went wrong. You can’t avoid mistakes and errors, but as the cyber leader, you need to make room for acknowledgment of progress and what’s going right.
Your cybersecurity culture has to be a safe place for this to occur so that feedback can be more positive and specific. You can still correct behavior and guide people toward best practices. If this never happens, employees will become disengaged and resentful. They’ll see you or the organization as the enemy, not the hackers.
These challenges are inherent in cybersecurity but not without a solution. Transforming technical professionals into excellent communicators and collaborators is the core of building your culture.
How to Build a Sustainable Cybersecurity Culture
No matter how mature or large your cyber department is, you can construct and foster a sustainable culture that decreases risk. As someone who has years of experience building resilient and adaptable technical teams, it is evident that culture was a people problem.
As a result, I developed strategies and initiatives to correct it in the Secure Methodology™. It’s a seven-step process that helps cyber leaders develop soft skills in their staff with the outcome of a cohesive team ready to protect an organization. Here’s how it applies to culture development.
Employees Need to Know Their Contributions
The seven-step guide touches on how employees see themselves in terms of the enterprise and its impacts. The problems with this are twofold. First, they often believe themselves to be individual contributors because they ascribe to a lot of black-and-white thinking. They want to remain solely in their lane, which causes siloes and fractures in collaboration and communication.
The second part is that they don’t feel valued or appreciated for what they do. As a result, they don’t know that what they do matters, which makes them complacent, elevating risk.
To address this, you need to work on acknowledgment, provide a clear vision of the role cyber teams play in company objectives, and champion constant communication.
A Shift to a Growth Mindset Is Imperative
You can either have a fixed or growth mindset, and cybersecurity culture only flourishes under the latter. When your technical employees are set in how they see cybersecurity and the world, they can’t grow. It’s not about learning new technical skills; they feel comfortable with this. Rather, it’s about changing perspective, which requires hard work.
If you can construct a culture that encourages growth and change, your people may be less afraid to do so. They have the potential to do this. It simply requires commitment.
Communication Is Everything
Communication includes the words we use, how we interact, and our listening ability. A lot of communication is actually nonverbal, and I can’t emphasize enough how crucial it is to understand that.
Typical technical communication is acronyms, jargon, and overcomplicating the simplest explanation. Cyber professionals have been indoctrinated in many ways to communicate in this way. It’s time for you to help them break these bad habits because they’re hurting all parties.
You’ll need to dedicate a lot of soft skill development to communication with exercises and resources. You also must lead by example, ensuring that your message is consistent and instructive. It becomes the bedrock of your cybersecurity culture, enabling your team to work as one.
Communication skills are also always in need of improvement and work. With any change to culture or new risk on the horizon, your team must continue using what they learn. That’s how it becomes culture — through daily use!
Focus and Distractions in a Dynamic Environment
Another component of building a cybersecurity culture is that the environment is so dynamic. As a result, focus can become disrupted, and distractions are plentiful. The best way I know to tackle this is by monotasking.
Monotasking requires concentrated work. It’s not a term that’s celebrated in the business world because it’s the opposition to multitasking. We’re brainwashed to multitask constantly; when we do, our attention strays. In cybersecurity, this becomes a threat.
The demands on cybersecurity never ease and require immediate responses. This paradigm won’t change. However, if your culture encourages monotasking, so that focus on specific tasks is distraction-free, your people will likely be more productive and effective.
Connecting with Others Means Shedding Self-Centered Thinking
A healthy cybersecurity culture focuses on cognitive empathy. It’s the notion of understanding the feelings of others and their perceptions. Empathy is the choice to connect with someone and accept their perspective. When present, it delivers many advantages in how you manage cyber risk because it fuels the belief that change and adaptation are good.
Again, empathy starts with you as a leader. If you demonstrate it regularly, it begins to weave its way into your culture. Making it a priority to educate your people on empathy and how to make it part of their skill set is critical to their remembering who the real enemy is — the hackers.
A Strong Cybersecurity Culture Thwarts Internal Threats
Cultivating a strong cybersecurity culture is something you have control over, which is rare in the field. If you promote one that values communication, collaboration, trust, acknowledgment, and empathy, you have an advantage over external threats. You can learn more about applying the Secure Methodology to culture by reading my book, The Smartest Person in the Room.
 Communication is a skill vital to every role in an organization. Without it, we make assumptions, and breakdowns occur in processes and workflows. It’s often the leading reason for dysfunction in a group. It has equal importance in cybersecurity. However, cybersecurity communication skills are often poor or nonexistent.
Communication is a skill vital to every role in an organization. Without it, we make assumptions, and breakdowns occur in processes and workflows. It’s often the leading reason for dysfunction in a group. It has equal importance in cybersecurity. However, cybersecurity communication skills are often poor or nonexistent. Communication is the core of any organization, department, or process. It’s a topic I talk about extensively in the world of cybersecurity. That’s why it’s step four of the Secure Methodology and why it’s a critical aspect of every effort.
Communication is the core of any organization, department, or process. It’s a topic I talk about extensively in the world of cybersecurity. That’s why it’s step four of the Secure Methodology and why it’s a critical aspect of every effort. Having effective communication skills is an asset in any career, even cybersecurity. It’s a soft skill that nicely complements technical ones. Having communication aptitude is a must for cybersecurity professionals. Without this cybersecurity soft skill, a lot can go wrong.
Having effective communication skills is an asset in any career, even cybersecurity. It’s a soft skill that nicely complements technical ones. Having communication aptitude is a must for cybersecurity professionals. Without this cybersecurity soft skill, a lot can go wrong.
 The advent of technology makes it easier for us to communicate with our staff and improve our business processes. However, it can also be a major risk to our organization: Hackers are lurking in every corner, waiting for the right time to steal information from us.
The advent of technology makes it easier for us to communicate with our staff and improve our business processes. However, it can also be a major risk to our organization: Hackers are lurking in every corner, waiting for the right time to steal information from us.
