 The first iteration of making development and operations a tandem was DevOps. The strategy married the two in a practical and tactical mode and cultural philosophy. The objective was to automate and integrate software development and IT. However, it left out a fundamental principle — security. That was rectified with the origination of DevSecOps — the trifecta of development, security, and operations.
The first iteration of making development and operations a tandem was DevOps. The strategy married the two in a practical and tactical mode and cultural philosophy. The objective was to automate and integrate software development and IT. However, it left out a fundamental principle — security. That was rectified with the origination of DevSecOps — the trifecta of development, security, and operations.
Security was previously an isolated segment of the process, coming at the end. Except that wasn’t very effective. Leaving security as an afterthought meant delays in new iterations and lots of rework, which was expensive. There was a realization that security shouldn’t be the red-headed stepchild but deserved a full seat at the table. Collaboration among all three can lead to many benefits, so why hasn’t every organization pivoted? And why should they now?
Secure by Design
The underlying foundation of DevSecOps is to be secure by design. Security is a consideration at the conception of the project, not an afterthought. Even in rapid deployment, which is part of today’s digital transformation schematic, security must be part of the concept.
DevSecOps and its importance to cybersecurity is that notion of everything developed and operated has consistency in security and that it’s scalable. The biggest clash in DevSecOps may be between your security experts and those who see security as a hindrance. This hurdle can seem insurmountable, and as a cyber leader, you may have to put yourself in a position to evangelize that security doesn’t have to impact agility.
Creating a Balance: Security and Agility
Business leaders in your organization demand velocity in development and operations. The reasons are apparent — greater efficiency, reduced costs, and more revenue opportunities. Those priorities may not be yours. You can understand the need for faster development to support these business objectives. Still, you’re also keenly aware that your company won’t meet its goals without security in applications and operations.
The question then becomes, how do you balance security and agility? From your perspective, you know that security and agility aren’t mutually exclusive. Security doesn’t halt agility and can support it. The misconception that security is a barrier to innovation isn’t new, yet it persists. It may even be present in your cyber team. As a result, you must make a case for security, knowing that your security mindset narrowly focuses on risk in a way that development and operations cannot.
Now, you’re at a crossroads of convincing technical and business stakeholders that all three can work harmoniously. There are plenty of guides to building DevSecOps, and I’m not going to rehash those. Rather, I want to show you how the Secure Methodology™ and DevSecOps have much in common.
Applying Secure Methodology Lessons to DevSecOps
As a refresher, the Secure Methodology is a seven-step framework that helps cybersecurity leaders transform their staff into effective communicators and collaborators. It’s a pathway to take technically adept folks who lack the foundational skills to be curious, innovative, and welcome growth. In a way, the Secure Methodology has many things in common with DevOps and DevSecOps cultures. In all three concepts, there are synergies, including:
- Collaboration and shared responsibility
- Accountability in every aspect of the cyber landscape
- Standardization around cybersecurity practices
- Aligning security with business objectives
- Increased transparency and communication
- Continuous learning and improvement
- High empathy and trust
These are all cornerstones of the Secure Methodology and DevSecOps. Next, we’ll go through the seven steps and how they can help you pivot your organization to a DevSecOps framework and culture.
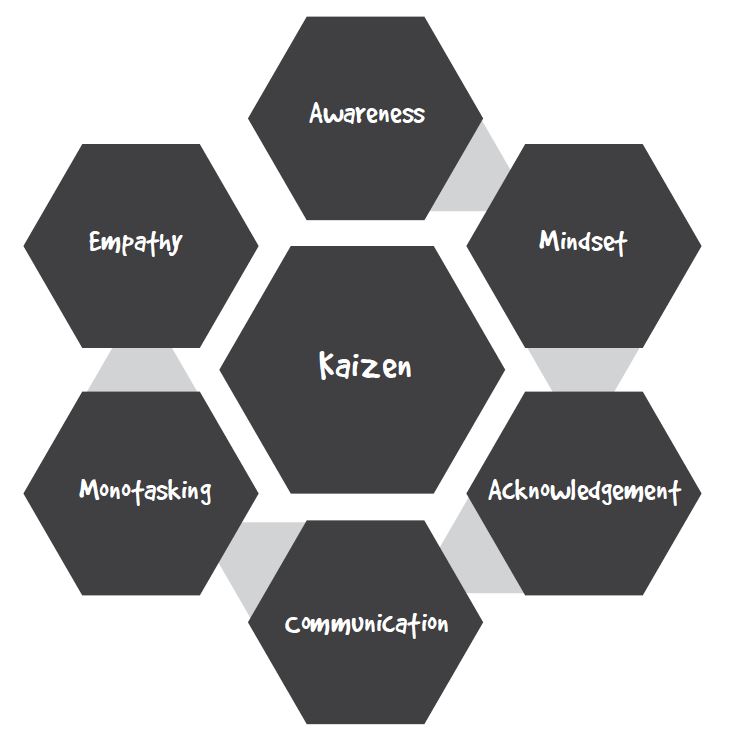
Step One: Awareness
Awareness is the first step because you can’t move any further without it. It’s about being aware of yourself and the behaviors you can control. Additionally, there is the awareness of others. To be a successful professional and person, you have to have both.
When awareness is missing, it causes issues, including inadequate communication, resentment, animosity, competition, and many other things that detract from security.
Awareness is a key component of DevSecOps from the position that all three parties must be aware of one another in such a framework. Development cannot move to operations without security, for example.
Using the tools of the Awareness step could help bridge the gaps between these groups and break them from their silos. The critical areas of focus should be:
- Perspective beyond a person’s limited view
- Respectful and transparent communication
Both things feed into the next step, Mindset.
Step Two: Mindset
Mindset impacts everything we do. When it’s one of growth, we see opportunities, encourage feedback, and embrace uncertainty. When it’s fixed, we do the opposite. A growth mindset is the goal. Without it, you’ll never achieve security by design because there’s no ownership and accountability.
The problem with technical (and nontechnical) people is that they run from the truth and feel comfortable only with what they know. That’s risky behavior in the realm of cybersecurity. Moving mindsets is really hard. Not all will be able to hack it, but if it becomes part of your cyberculture, it’s ideal for a shift to DevSecOps, which is all about transparency and honesty.
There are some exercises to help with transformation as part of the Secure Methodology that can help with this. Another thing to note is that you have to talk about mindset in general when you have development, operations, and security staff together. You are outlining how each person needs to adapt their mindset for everyone to find success.
Step Three: Acknowledgment
Next is Acknowledgment, and it’s a big challenge for cybersecurity teams. There is a general lack of appreciation from supervisors to employees happening in every organization worldwide. The nature of cybersecurity is to focus on what went wrong because something always will. I’m asking you to refocus on all the things that go right every day.
Acknowledgment is all about feedback, which is critical in DevSecOps too. Not all feedback will be positive, but when it’s not, it should be constructive so that people learn from what occurred instead of being humiliated. Such actions lead to resentment, disengagement, and turnover, and that’s not good for any company or its security posture.
The act of acknowledging others makes people better at what they do. It builds their confidence and helps them grow their skills and be better collaborators and communicators, and every DevSecOps culture needs that to thrive.
Step Four: Communication
Communication is the most important step. It will make or break any team or company. Without consistent and transparent communication, you’ll never achieve DevSecOps, even if everyone’s on board. It simply just doesn’t work.
Communication is about more than words. It’s how they are said and the nonverbal elements as well. The biggest communication barrier is often geek speak. Security, development, and operations may all have their own versions of this. They believe it makes them superior. In reality, it causes confusion, frustration, and distrust, which aren’t the kind of emotions you want in any room.
You and your entire organization must make improving communication a priority. You have to create an environment that appreciates clear and positive communication. I recommend looking at the exercises in my book for more details on this so that communication becomes an asset, not a weakness.
Step Five: Monotasking
Monotasking means concentrating on one task at a time, which is crucial in cybersecurity. The problem is that society, in general, discounts it as not being flexible or able to juggle multiple things. We’ve been conditioned to believe we should be multitasking. So, you have the challenging job or rewiring brains to understand that multitasking causes risk!
Well, it may not solely be on your shoulders because DevSecOps and its proponents will agree. While it’s the convergence of three areas, DevSecOps appreciates workflows and processes that build on each other. You don’t move to the next one until you finish the first one. If you can retrain your team to focus deeply on specific tasks without distractions, velocity and productivity will actually soar.
Step Six: Empathy
You may be wondering what empathy has to do with cybersecurity and DevSecOps. Except we’ve been building up to this with discussion around awareness, acknowledgment, and communication.
Empathy makes us human in many ways, but it’s become something lacking in the world and at work. At the end of the day, we’re all human, and if we can appreciate the perspective of others, we can be better problem-solvers and collaborators. It easily applies to DevSecOps because three independent groups have to empathize with the others and understand their position for it to work.
If you can build empathy in these teams, you can move to the final step, Kaizen.
Step Seven: Kaizen
Kaizen is a Japanese term meaning “continuous improvement.” As people and professionals, we always want to be improving. We want the same for our development, operations, and security. It’s all about progress, no matter how small, as long as it’s constant.
It’s the ideal ending of the process, but not one that ever ends. It’s the same for DevSecOps. It’s a circle, not a line, after all.
You can learn more about the Secure Methodology and how it aligns with DevSecOps by reading my book, The Smartest Person in the Room. Check out my Secure Methodology course too.
 The advent of technology makes it easier for us to communicate with our staff and improve our business processes. However, it can also be a major risk to our organization: Hackers are lurking in every corner, waiting for the right time to steal information from us.
The advent of technology makes it easier for us to communicate with our staff and improve our business processes. However, it can also be a major risk to our organization: Hackers are lurking in every corner, waiting for the right time to steal information from us.

