Cybersecurity certification exams are not easy to pass. According to Concise-courses.com, 70% of surveyed CISSP test-takers reported that the CISSP exam is “difficult.” As such, some individuals seeking credentials in the field of cybersecurity have looked for ways to cheat their way into certification.
These cybersecurity exam cheats (also known as paper tigers), however, cost everyone – the company issuing the test, those offering credentialing, and the cybersecurity industry at large. And, in the long run, they certainly don’t pay off for the student.
Dirk Groben, a cybersecurity professional who succeeded on the CISSP exam on his first try reports that “the exam was very difficult because it’s wide-ranging and does not just include technical information security. It’s a matter of understanding the whole picture for security and not just looking at parts. This new vision increased my professional experience with IT-Security cases. I did pass the first time but really took the full exam time of 6 hours.”
One might ask the question – why would students who are seeking entrance into the cybersecurity field – a field that strives to maintain the integrity of systems – find themselves willing to cheat on a credentialing exam? Proctoru.com attributes the willingness to cheat to pressure. “Pressure from parents. Pressure from peers. Pressure to keep scholarships. Today’s high school students face massive amounts of pressure to do well so they can get into a good college, then to do well in college so they can have a sturdy, competitive career afterward. Some students will go to any length in order to not disappoint their parents or themselves.”
Though cheating one’s way through a class or into a job might sound like a workable solution to a desperate student, in the long run, online cheating venues don’t offer any guarantees of a pass, nor do they ensure a test-taker success in the cybersecurity field. Unfortunately, however, resources for online cheating are readily available.
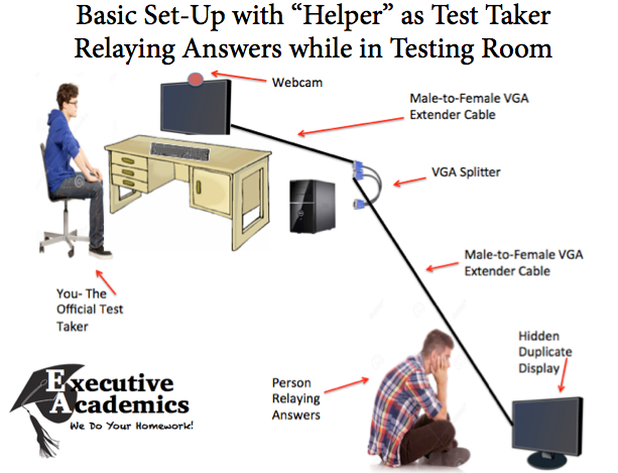 Cheating Online Proctoring. Source: http://www.executiveacademics.com/single-post/2016/1/5/Beating-Cheating-and-Defeating-Online-Proctoring
Cheating Online Proctoring. Source: http://www.executiveacademics.com/single-post/2016/1/5/Beating-Cheating-and-Defeating-Online-Proctoring
Executiveacademics.com released an article in 2016 that essentially teaches test takers how these cheating resources work. The article states: “We signed up for a few classes that required multiple proctored exams in an attempt to determine the best way to game the system for different online proctoring companies. With a bit of creativity, we designed a way to cheat online proctoring sites using a specific hardware set-up and a “helper” person.”
Other common ways to cheat include capturing the test, using a small-button camera, or utilizing brain dumps found online. What are brain dumps? Margaret Rouse, with Whatis.techtarget.com explains: “someone who has taken an exam might perform a brain dump by writing out as many of the questions as they remember, for distribution as a study guide for other people who intend to take the same exam.” According to Rouse, “brain dump Web sites for exam preparation purposes are fairly common, especially for computer-related certification programs.”
Though some brain dump sites manage to avoid detection, the risk of getting caught as involved in brain dump cheating scandals are steep. Rouse describes an incident that occurred In January 2003: “Robert Keppel was sentenced to 12 months plus a day in prison and fined $500,000 for maintaining a brain dump (cheatsheets.com) that sold Microsoft Certified System Engineer (MCSE) and Microsoft Certified Solution Developer (MCSD) exam questions.”
The ready availability of cheating mechanisms, and the willingness of students to seek them out, presents a major issue for test administrators, credentialing bodies, and for the cybersecurity field. The more cheating that takes place, the shakier will be the skills and professionalism of those holding certifications. According to Securelink.com, when it’s proven that cheating on a particular platform is possible, the vendor can suffer “brand damage, questions about its tech, and the ability to offer secure services.”
What can governing agencies do to control cheating and ensure that those endowed with cybersecurity certifications legitimately earned those credentials? Kenneth Brown, an Associate Dean of Undergraduate Programs for the Business School at UI, explains on ProctorU.com that accountability is difficult to enforce because of the difficulty that regulating bodies face in going after companies that facilitate cheating. “They are not U.S.-based,” says Brown. “They’re not tangible, necessarily.”
But cheating one’s way into a cybersecurity field that aims to prevent crimes via security breaches is a poor beginning for any IT student. Test-takers must realize that scamming the system to find brain dumps or access test questions may not even help when it comes to passing a certification exam. The reason certification exams are in place to begin with is to allow an individual to assuredly prove that he or she has the skills needed to do the job. Cheating through a cybersecurity exam does nothing to equip a candidate to handle the actual, challenging work of cybersecurity. Dirk Groben, with IT solutions, states: “I’ve read books for CISSP examinations. But forget the brain dumping stuff. The exam is about thinking different.”
If you’re thinking about cheating an exam, do yourself and the industry a favor and self-identify as a paper tiger.
 As much as every organization wants to believe they are cyber secure, the reality paints a different story. Cybersecurity methods continue to evolve with an emphasis on tactics and technology. This progression of companies and government agencies follows the cybersecurity status quo that it’s a hardware and software issue.
As much as every organization wants to believe they are cyber secure, the reality paints a different story. Cybersecurity methods continue to evolve with an emphasis on tactics and technology. This progression of companies and government agencies follows the cybersecurity status quo that it’s a hardware and software issue.