 According to the Information Systems Security Association (ISSA), we’re facing a cybersecurity skills crisis. Their recent report calls the gap in qualified individuals a “rapidly widening business problem,” claiming businesses are investing their resources in the wrong places when it comes to cybersecurity.
According to the Information Systems Security Association (ISSA), we’re facing a cybersecurity skills crisis. Their recent report calls the gap in qualified individuals a “rapidly widening business problem,” claiming businesses are investing their resources in the wrong places when it comes to cybersecurity.
ISSA partnered with Enterprise Strategy Group (ESG) to look at the state of qualified cybersecurity professionals in the workforce. Around 70% of respondents to their survey said they felt a lack of cybersecurity skills within their organization was affecting their company. According to the cybersecurity organization (ISC)², almost three million cybersecurity jobs needed to be filled globally as of 2018.
Most people agree that this is a serious problem. The lack of qualified professionals at major businesses with knowledge in cybersecurity is exacerbating data breaches, and has been called an “existential threat to our national security.” What there doesn’t seem to be a consensus on is how that problem should be solved.
Are There Really Not Enough Qualified People to Fill the Cybersecurity Skills Gap?
The short answer seems to be no. Rather, the problem seems to lie with the paths made available to talent looking to get into the cybersecurity industry.
For a long time, the university path has been the main place students get recruited into cybersecurity jobs. Organizations recruit from universities, and many require a college degree as part of their job descriptions for cybersecurity roles. But there are thousands of talented people that miss out on these job opportunities simply because they don’t choose to go to college.
In an article for Forbes, cybersecurity contributor and CEO of Immersive Labs James Hadley argues that the cybersecurity skills gap won’t be mitigated through the classroom. He argues that self-taught, talented people should be recruited and trained by organizations before they take their talents to the wrong side. He writes:
“The world is desperate for cybersecurity talent, yet the sector limits entrants and clings to obsolete training methods. As the skills gap grows and organizations become increasingly vulnerable to ever-more-complex threats, the need for a diverse pool of cybersecurity experts to learn in real-time, rather than a classroom, strengthens.”
Hadley uses the example of 22-year-old Daniel Kelley, who hacked the telecom company TalkTalk, stole the data of thousands of users, and used it for blackmail as an example of what could happen if people who feel snubbed by the system use their talents for ill. Kelley didn’t make the grade required for a computer course and attacked TalkTalk out of a desire for revenge. He could’ve ended up using his skills to help instead of hurt, Hadley argues, had that path not been closed off to him.
Companies don’t want to train employees, preferring that they come to the job with the skills they need already, but the nature of cybersecurity work demands constant retraining and maintenance of those skills. There are qualified people ready to help stop the next cybersecurity threat if companies are willing to adapt to them.
How Can Companies Fill The Gap?
The threat of cyberattacks and hacking isn’t going away. In fact, they’re likely to increase as time goes on and the technology both companies and hackers use becomes more sophisticated. That’s why businesses should do everything they can to make themselves resilient to cyber threats. How can they do that?
First, hire and train the right people. Provide them with the time and resources they need to continually develop their skills to match the changing threat and technological landscape. Devote more of the company budget to cybersecurity. Currently, 49% of companies say that cybersecurity is a budget priority, but pros say that figure should be closer to 60%.
A shift away from the traditional job requirements of a university degree path would allow for the scouting, hiring, and training of the right people. Instead of academic background, those in the cybersecurity field would be better served by looking at a candidate’s skill sets. Do they have the skills needed for the job, even if they don’t have the degree? If they do, invest in that talent.
A few of the skills necessary for cybersecurity jobs:
-
Relevant past work experience,
-
Ability to understand advanced cybersecurity concepts,
-
Cybersecurity certifications,
-
Strength in non-technical soft skill areas.
University education can help, but it shouldn’t be the only factor in determining whether a potentially promising candidate in the cybersecurity field gets turned away, especially if that candidate could broaden the diversity of the field. Women represent only 23% of the cybersecurity workforce, according to (ISC)², and that number is after they broadened the definition of who works in cybersecurity.
It isn’t just companies that can help close the gap and guide more capable people into a cybersecurity career. Government initiatives like the UK’s Cyber Discovery free training program can help people explore their interest in IT, and ultimately decide that it’s a good career for them. State and federal governments in the U.S. should implement their own programs to seek out and support talent in a similar fashion.
Part of solving this problem will be getting the word out. Careers in IT and cybersecurity aren’t talked about as widely as more traditional paths like doctors or nurses, or trendier digital careers like YouTuber or Instagram influencer. But the fact is that people who have these jobs hold them a long time, are satisfied with the work they do and are compensated very well for their efforts. If more people knew that, starting at a younger age, they might find a place for their skills where they didn’t think one existed.
Companies can put themselves at the front of the pack by taking the initiative to find and recruit top talent outside the conventional pipeline. And they can do it by being willing to invest the time and money in proper, ongoing training. The cybersecurity skills shortage isn’t all that frightening if you know where to look to close the gap and are willing to take action.
 Land a new and better cybersecurity job with these LinkedIn tips.
Land a new and better cybersecurity job with these LinkedIn tips.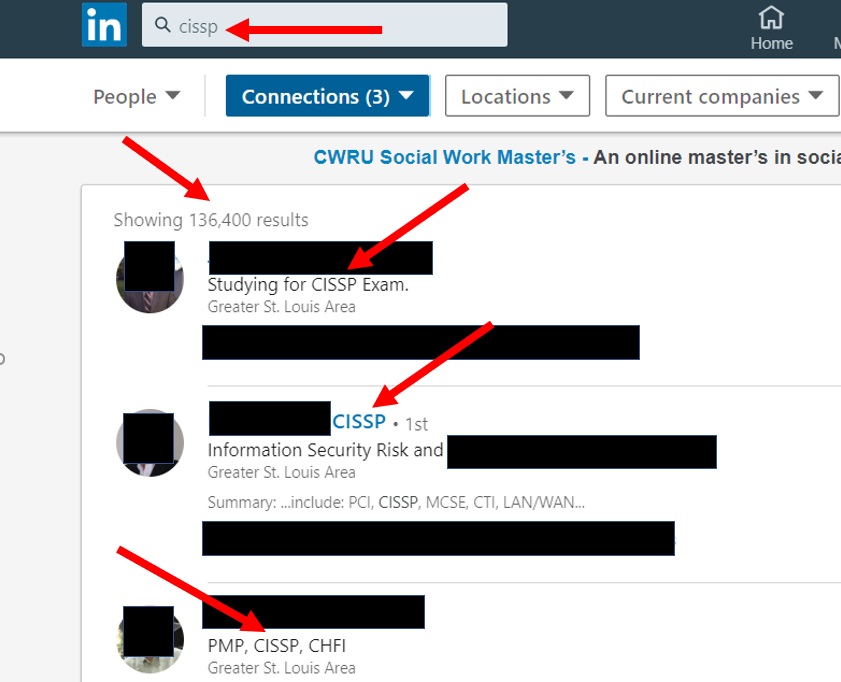


 Hiring practices are different for every field, and for cybersecurity professionals, there are many opinions. In a growing and evolving industry, some standardization exists, including a significant focus on certifications. But do certifications equal talent? Not always. As a cybersecurity leader with years of experience building teams, I want to teach you how to hire cybersecurity professionals so they and your organization can be successful.
Hiring practices are different for every field, and for cybersecurity professionals, there are many opinions. In a growing and evolving industry, some standardization exists, including a significant focus on certifications. But do certifications equal talent? Not always. As a cybersecurity leader with years of experience building teams, I want to teach you how to hire cybersecurity professionals so they and your organization can be successful.




