Finding qualified and skilled talent has been a struggle in cybersecurity for years. According to data, that’s only getting harder. Exasperating the cybersecurity workforce shortage is the fact that retaining employees is challenging. Cybersecurity workforce retention is as important as your recruitment strategies.
Finding qualified and skilled talent has been a struggle in cybersecurity for years. According to data, that’s only getting harder. Exasperating the cybersecurity workforce shortage is the fact that retaining employees is challenging. Cybersecurity workforce retention is as important as your recruitment strategies.
So, how do you keep cyber professionals on the job? It’s not an easy answer, as so many factors impact this. However, you can build a retention plan alongside your recruitment strategy. In this post, we’ll uncover why turnover occurs and how to create a culture and environment that will make them stay.
The Cybersecurity Workforce Retention: State of the Industry
A study from the ISACA found that 60% of cyber leaders said it was difficult to retain cybersecurity professionals, up 7% year-over-year. The survey outlined why it’s happening, with these being the top reasons:
- Recruited by other companies (59%)
- Compensation and incentives (48%)
- Few promotion and development opportunities (47%)
- The high stress of the job (45%)
- No management support (34%)
Some of these challenges are easier to combat than others. Currently, cybersecurity jobs are greater than those available to fill them. A study estimated that over 3.4 million cyber jobs are available, which will only increase. As a result, other companies will try to lure away your employees, even if they aren’t actively looking for another job. How they respond to this will depend on how they feel about working for you in terms of money, autonomy, support, and satisfaction.
Compensation is another tricky area. Competitors may be offering more money. While that’s a critical part of why people work, money may not be the top factor in retention. Regardless, depending on their experience, role, and market, you should pay your team a fair wage. With the cost of living increasing, you must keep up with this.
Next is development, which is something you can control. Continuing to train and upskill your team shows you’re investing in them and their future. You should also be clear with them about the opportunities to advance.
Stress is inevitable in almost any job. Cybersecurity is a dynamic industry with fire drills all the time. Focusing on ways to destress workers should be part of your culture. It could be rewarding your team with social or team-building activities. Having an open door for employees to share their experiences with you and their stress can also be helpful.
Finally, you have complete purview over management support. As a leader, you have to earn and keep the respect of your team. Being a great leader requires you to communicate honestly, listen intently, acknowledge their work, and support them in any way you can.
Addressing these common reasons for turnover is critical for your organization because its impact is considerable.
The Impact of Turnover
An inability to retain staff affects many aspects of operations. Being understaffed creates more risk because everyone’s stretched thin. It’s easy to miss key things when someone is overwhelmed. Turnover also prevents your ability to be more strategic because you’re in a reactive mode versus a proactive one. Productivity suffers as well.
Turnover also costs you money. The average cost of hire is $4,700 and could be even greater considering how in demand these roles are. It’s in your best interest to retain your technical folks, which isn’t easy. You may be looking at many methods to decrease turnover, including increasing wages and benefits, allowing for flexible work, asking for feedback from your team to propel improvement, and providing the right tools to do the job.
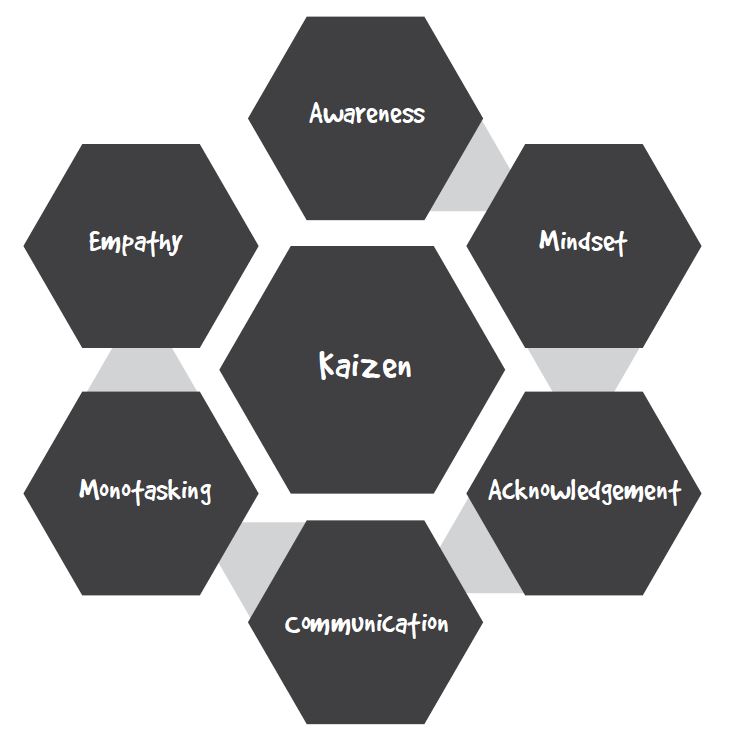
Those are all good things to have, but retention has much to do with engagement, satisfaction, feeling valued, and having respect for leadership. These things can mean more than money, which is why applying the Secure Methodology™ to cybersecurity workforce retention makes sense. It’s a seven-step guide that defines a roadmap to transform technical people into highly communicative and collaborative professionals.
Let’s see how each step can support retention.
Applying the Secure Methodology to Cybersecurity Workforce Retention
With every step of the Secure Methodology, there are lessons to learn that impact retention. Here’s how to use these in your organization.
Step One: Awareness
Tapping into awareness is an important attribute to have in life and work. We all have blind spots, but some are bigger than others. Without being aware of these, there are consequences. It negatively impacts relationships and erodes trust. Without being aware, your team doesn’t realize how their behavior affects others and the environment. Things can become toxic very fast. If those things are lacking, it’s easy to see why some would want to leave.
Awareness means being cognizant of your blind spots and working to address them. A more aware team will be more collaborative and communicative. Here are some ways that this can support retention:
Coaching
Coaching is vital to broadening awareness. If you can open the eyes of your team in a conducive way, they may have “aha” moments. Shifting their stance from being self-centered allows people to get a better perspective.
Language
Using specific, relatable language helps technical people better understand expectations and culture. When there’s no confusion about where everyone should focus, they will likely feel more empowered.
Motivation
Understanding motivations is critical to unlocking awareness. Tapping into what makes them tick helps strip away some of the technical posturing cyber professionals often do. Knowing their motivations allows you to personalize how you support and coach them.
Step Two: Mindset
There are two types of mindsets — fixed and open. Many technical folks have fixed mindsets with no desire to change, learn, or grow. However, it doesn’t mean they have to stay that way. Fixed mindsets are poisonous to retention. Even if one in the group is this way, it can taint it for others. When we’re fixed, we refuse to move.
A growth mindset is freeing and enables people to be flexible and adaptable, which is necessary for cybersecurity. Evolving a fixed mindset to a growth one is possible, but it requires commitment from you and the employee.
Some key results of a fixed mindset include:
- The ability to reflect on situations and understand how to handle it differently.
- Healthier and consistent communication.
- A culture that welcomes growth personally and professionally.
- Growth mindsets can be a significant reason employees stay with your organization.
Step Three: Acknowledgment
Acknowledgment is scarce in technical fields. Yet, it’s so crucial to retention. Your employees want appreciation for the work they do. Its absence is because most cyber leaders only respond to things when they go wrong. The small wins everyday matter so much to your people, so you must become vigilant about feedback.
Your approach to acknowledgment should include:
- Being positive by looking at what went right first
- Specificity in your feedback
- Immediately offering feedback in the moment
- Praise in public and relay ways to improve in private
- Consistency in how you address acknowledgment
Lack of appreciation and lack of feeling valued are two primary reasons why people leave their jobs. If your people don’t receive acknowledgment, they’ll actively seek another job.
Step Four: Communication
Communication is part of every step in the Secure Methodology, along with having its own step. It is, without a doubt, the most critical part of a thriving culture and support to retention. You probably know there are communication issues among your technical folks. It doesn’t mean they aren’t articulate. Rather, their communication styles are often too aggressive, overly complicated with geek speak, and always on the defense. They also suck at listening, the other component of communication.
This storm of dysfunction will have people, often your best, running away from your organization. Thus, it’s critical to make communication the foundation of your culture and retention strategy. Here’s how to use it:
- Be honest and transparent as a leader.
- Move away from overly technical language and simplify the message.
- Encourage open discussion and dialogue that’s respectful.
- Praise your people when they make adjustments in communication.
- Practice active listening in exercises, so they grasp how crucial it is.
If you can lay out these tenets, your people will likely see the value and follow you. If some still don’t realize it, they may be dragging others down. In some cases, you may have to let those folks go, so they don’t make it unbearable for everyone else.
Step Five: Monotasking
Monotasking is focusing on one thing, the opposite of multitasking. Many describe multitasking as an excellent quality, but it can actually hamper productivity. Forcing multitasking can make your people feel pulled in many directions. Those feelings create animosity and dissatisfaction. So, remove this pressure and instead recommend blocking time for specific tasks, meetings without distractions, and saying “no” to some things that aren’t urgent.
Step Six: Empathy
Empathy is a valuable quality to have. In terms of cybersecurity, cognitive empathy is essential for a healthy environment. It means that others can understand the feelings and perspectives of others. Without it, you have no team or human connection, and you need those to retain your people. All the things you put in place to get to this step support the building of empathy. Developing this in your team enables a trust factor and creates more satisfaction.
Step Seven: Kaizen
The final step is kaizen, which is a Japanese term. When translated into English, it means “continuous improvement.” So, this step isn’t an end to the journey; it’s how to sustain it. If your team believes in this process, they’ll want to continue identifying ways to improve and follow through with them. When kaizen is part of your cybersecurity culture, your technical folks will evolve and realize that this is where they can continue learning and growing.
Retaining your workforce won’t be easy. With the Secure Methodology, you have a framework. You can go more in-depth by reading my book, The Smartest Person in the Room, and viewing the Secure Methodology course.
 The cybersecurity talent pipeline is facing the same challenges as many industries. A strong job market and low unemployment mean that many well-qualified professionals aren’t actively seeking new jobs. As a result, cybersecurity needs to look to the latest generation entering the workforce, Gen Z. Gen Z is a unique generation, which makes the ability to
The cybersecurity talent pipeline is facing the same challenges as many industries. A strong job market and low unemployment mean that many well-qualified professionals aren’t actively seeking new jobs. As a result, cybersecurity needs to look to the latest generation entering the workforce, Gen Z. Gen Z is a unique generation, which makes the ability to  Creating a cybersecurity culture isn’t a novel idea. It’s one that’s been around for some time, as the field and organizations realized that cybersecurity isn’t just about tools, protocols, and technical aptitude. Culture is much more about the people and, as a result, makes it much harder to build and sustain. People are unpredictable and don’t always have the skillsets to participate in culture. There’s an additional component of cultural manifestation, and it revolves around innovation. So, how do you develop a cybersecurity culture of innovation?
Creating a cybersecurity culture isn’t a novel idea. It’s one that’s been around for some time, as the field and organizations realized that cybersecurity isn’t just about tools, protocols, and technical aptitude. Culture is much more about the people and, as a result, makes it much harder to build and sustain. People are unpredictable and don’t always have the skillsets to participate in culture. There’s an additional component of cultural manifestation, and it revolves around innovation. So, how do you develop a cybersecurity culture of innovation? Hiring practices are different for every field, and for cybersecurity professionals, there are many opinions. In a growing and evolving industry, some standardization exists, including a significant focus on certifications. But do certifications equal talent? Not always. As a cybersecurity leader with years of experience building teams, I want to teach you how to hire cybersecurity professionals so they and your organization can be successful.
Hiring practices are different for every field, and for cybersecurity professionals, there are many opinions. In a growing and evolving industry, some standardization exists, including a significant focus on certifications. But do certifications equal talent? Not always. As a cybersecurity leader with years of experience building teams, I want to teach you how to hire cybersecurity professionals so they and your organization can be successful.