There are many ways to land a job that requires the CISSP (Certified Information Systems Security Professional) or any other cybersecurity certification. In this post, I share three methods to empower you to find your ideal job, leveraging your CISSP (or any other) certification. I hope these techniques enable you to land a job in cybersecurity that resonates with you.
There are many ways to land a job that requires the CISSP (Certified Information Systems Security Professional) or any other cybersecurity certification. In this post, I share three methods to empower you to find your ideal job, leveraging your CISSP (or any other) certification. I hope these techniques enable you to land a job in cybersecurity that resonates with you.
I use CISSP throughout this example. You can easily use this tactic with other cybersecurity certifications, such as the Security+.
#1: Research CISSP Job Openings
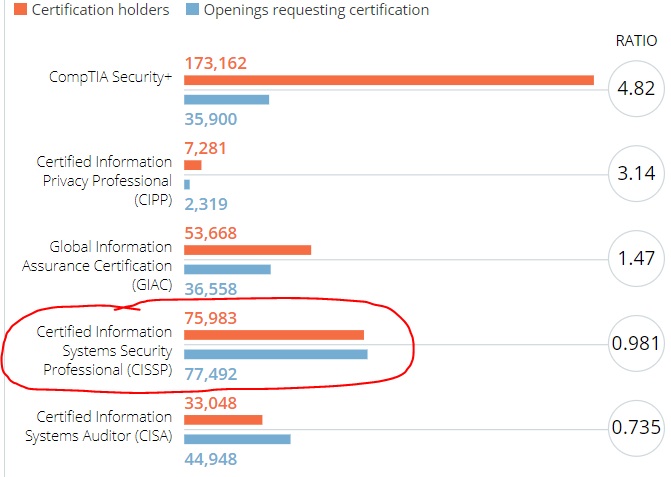
You should research CISSP job openings for where you are considering moving or the location you are seeking a job. According to CyberSeek, there are currently 77,492 open jobs in the United States that require the CISSP certification. Of the 77,492 open CISSP jobs, 2,031 are in the Public Sector, and 75,465 are in the Private Sector.
Job openings in the United States that require the CISSP certification. The orange number represents CISSP certification holders.
The blue number represents openings requesting the CISSP.
If you live in Arkansas and want to stay in Arkansas, as an example, there are 265 open CISSP jobs in the entire state of Arkansas.
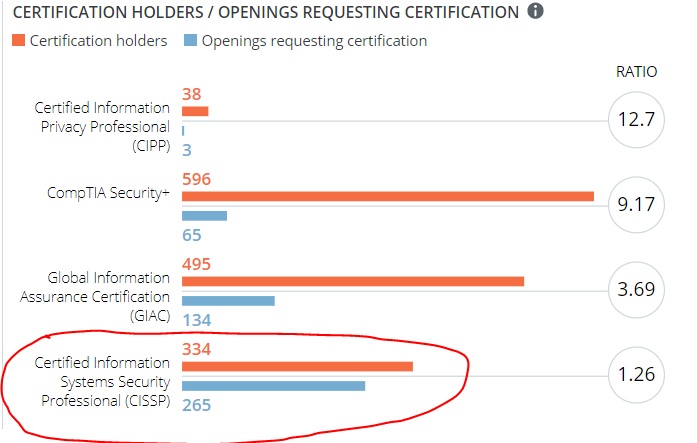
If you want to move to Texas, for example, there are 6,333 open CISSP jobs in Texas.
#2: Determine Which Organizations Hire People with the CISSP Certification
This technique involves you actively seeking a CISSP job.
There are several paths you can take:
-
you can work for the DoD as an actual DoD employee (civilian or military)
-
you can work for the DoD as a contractor
-
you can work in the private sector
Steps to become part of the DoD as a DoD civilian or member of the military are beyond the scope of this article. I will focus on numbers two and three above. If you are seeking a job as a DoD contractor or in the private sector, the process is the same because private companies that have DoD contracts hire DoD contractors. Private companies also hire CISSPs for private sector work.
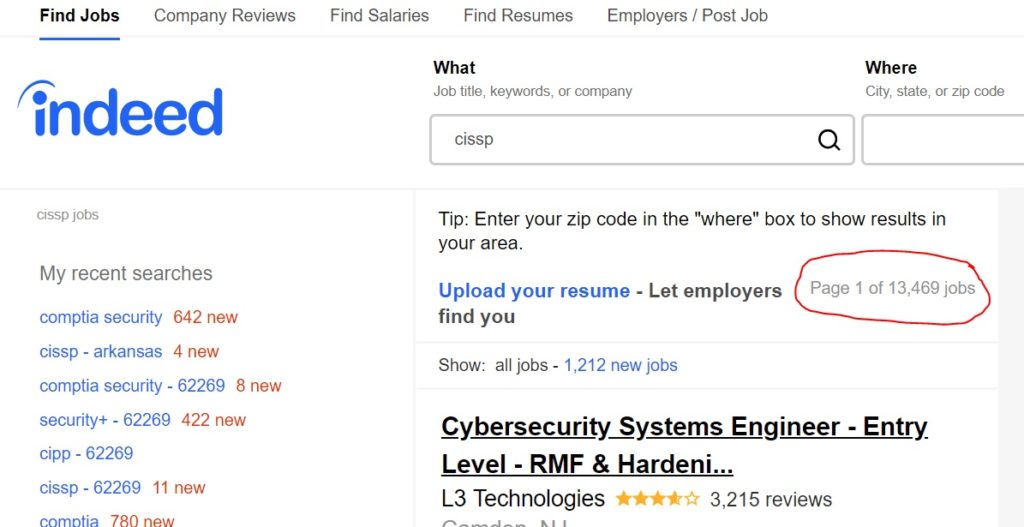
A good place to determine which companies are hiring CISSPs is indeed.com. As of this writing, there are 13,469 open CISSP jobs in the United States.
According to indeed.com, the company Deloitte has 514 open CISSP jobs, and Washington, DC has 765 openings for people with the CISSP certification.
Another source to determine which organizations are hiring CISSPs is LinkedIn. Search “CISSP” on LinkedIn and set the focus of the results to “Jobs.”
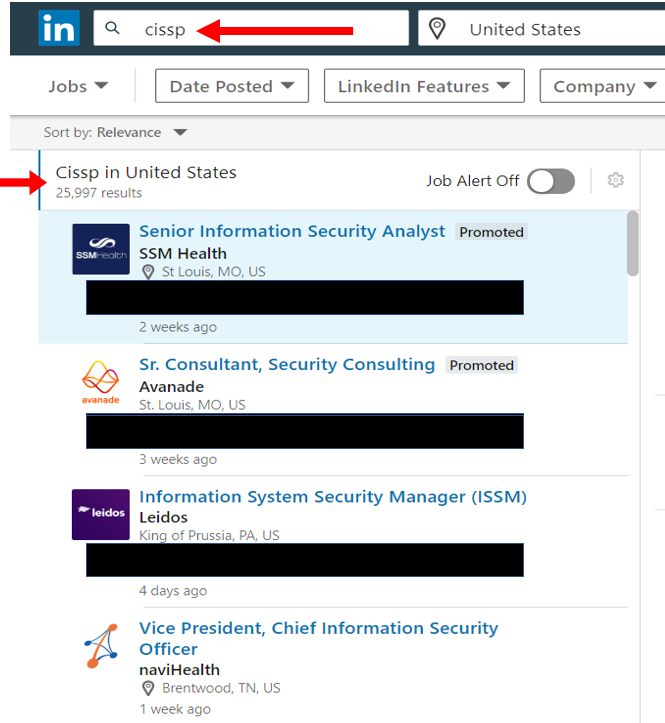
As you can see from the screenshot, there are 25,997 open jobs in the United States that required the CISSP certification.
#3: Update your LinkedIn profile with your CISSP certification
This technique involves you passively seeking a CISSP job.
Many employers, recruiters, and headhunters use LinkedIn to search for people with the CISSP certification. Listing your CISSP certification on your LinkedIn profile will make you show up in searches for “CISSP.”
In the screenshot above, I searched for CISSP, then switched the results to “People.” As you notice, one guy even listed “Studying for CISSP Exam” in his LinkedIn “Headline” and he showed up. The second person put it after their name, like “John Smith, CISSP”. The third person listed the CISSP certification as their LinkedIn Headline. Any of these approaches work to get the attention of employers, recr
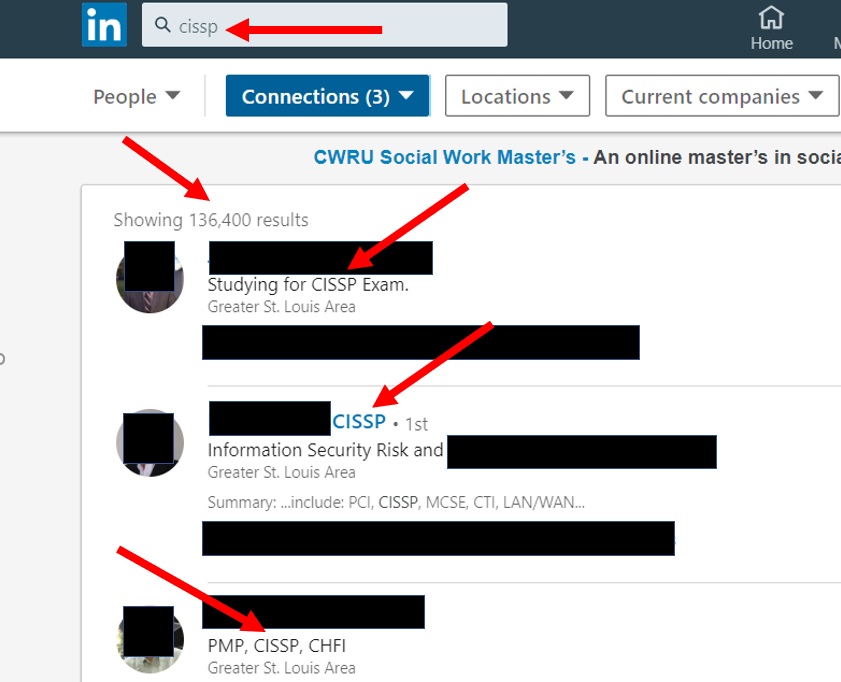
uiters, and headhunters. Just be prepared to be bombarded with “incredible opportunities” and lots of new connection requests.
Conclusion
I hope you find these strategies useful in your hunt for your ideal cybersecurity job. Best of luck!
 Land a new and better cybersecurity job with these LinkedIn tips.
Land a new and better cybersecurity job with these LinkedIn tips.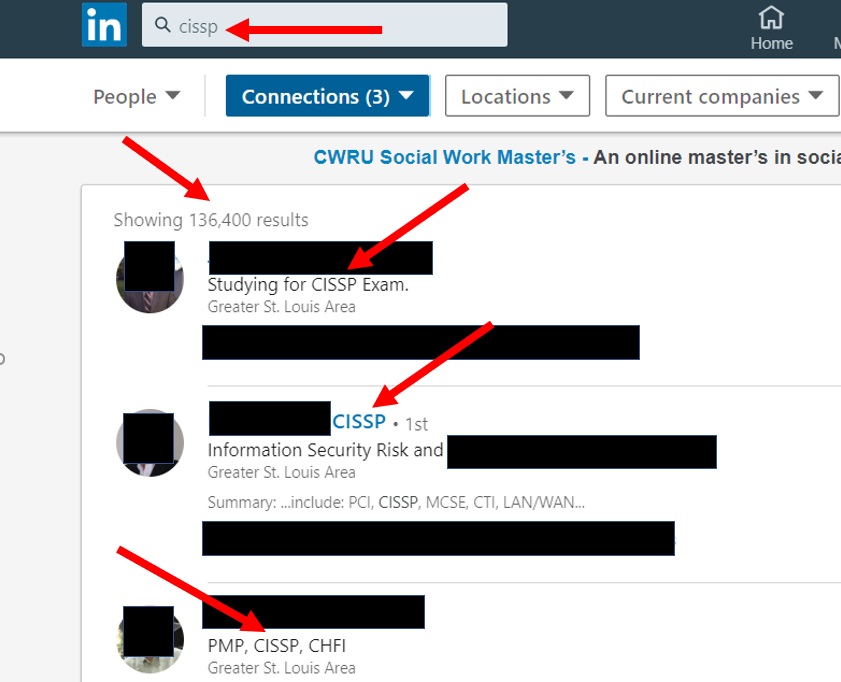


 Hiring practices are different for every field, and for cybersecurity professionals, there are many opinions. In a growing and evolving industry, some standardization exists, including a significant focus on certifications. But do certifications equal talent? Not always. As a cybersecurity leader with years of experience building teams, I want to teach you how to hire cybersecurity professionals so they and your organization can be successful.
Hiring practices are different for every field, and for cybersecurity professionals, there are many opinions. In a growing and evolving industry, some standardization exists, including a significant focus on certifications. But do certifications equal talent? Not always. As a cybersecurity leader with years of experience building teams, I want to teach you how to hire cybersecurity professionals so they and your organization can be successful. Almost every industry has certifications. Some carry more weight than others, but it’s clear there’s a trend of over-certification in cybersecurity. Most cybersecurity certifications aren’t hard to obtain and thus are not an illustration of someone’s expertise. The industry is creating many
Almost every industry has certifications. Some carry more weight than others, but it’s clear there’s a trend of over-certification in cybersecurity. Most cybersecurity certifications aren’t hard to obtain and thus are not an illustration of someone’s expertise. The industry is creating many  As much as every organization wants to believe they are cyber secure, the reality paints a different story. Cybersecurity methods continue to evolve with an emphasis on tactics and technology. This progression of companies and government agencies follows the cybersecurity status quo that it’s a hardware and software issue.
As much as every organization wants to believe they are cyber secure, the reality paints a different story. Cybersecurity methods continue to evolve with an emphasis on tactics and technology. This progression of companies and government agencies follows the cybersecurity status quo that it’s a hardware and software issue.