 It’s a new year, and that means new challenges and opportunities for the cybersecurity workforce. Currently, the job market remains healthy, with another 223,000 jobs added in December 2022 and unemployment falling to 3.5%. Rumblings of a recession and an uncertain economy remain, and big tech, including Meta, Amazon, Twitter, and Google, issued layoffs. However, the landscape for recruiting, hiring, and retaining cybersecurity talent remains a significant problem.
It’s a new year, and that means new challenges and opportunities for the cybersecurity workforce. Currently, the job market remains healthy, with another 223,000 jobs added in December 2022 and unemployment falling to 3.5%. Rumblings of a recession and an uncertain economy remain, and big tech, including Meta, Amazon, Twitter, and Google, issued layoffs. However, the landscape for recruiting, hiring, and retaining cybersecurity talent remains a significant problem.
So, how can organizations, big and small, address these problems, and where will the market shift?
The Workforce Grew But Remains Understaffed
The ISC 2022 Cybersecurity Workforce Study reported that the global cybersecurity workforce grew to over 4.6 million, an 11.1% year-over-year increase. The study estimated that over 3.4 million jobs remain unfilled even with this increase. This gap created genuine concern for staff, with almost 70% feeling there aren’t enough workers to be effective. Survey respondents also said that significant shortages increased risk. The cumulative effect of understaffing has real consequences, per the study, including:
- Lack of time to perform proper risk assessment and management
- Oversights in procedures and processes
- Slowing down the patching of critical systems
- Training deficiencies
- Misconfigurations of systems
Another study found that 80% of organizations experienced at least one breach in the last year, attributing it to a lack of cybersecurity talent or awareness.
Any cybersecurity leader likely has the same concerns. When there aren’t enough people, everyone is stretched thin. Corners get cut, and people get defensive and burn out. It’s an environment that could expose any company to more threats while vulnerabilities go unnoticed. Additionally, those coming into the industry often don’t have the necessary skills to contribute. They may have the technical aptitude but need training in real-life cyber work and honing soft skills.
So, if there isn’t enough qualified talent, how do you fix it? You’ll need new candidates to enter the industry and retain your current employees.
Cybersecurity Talent Pipelines Are Running Dry
It would be easy to think that younger generations all want to work in technology. They are digital natives, but that’s not exactly true. Only 9% of millennials had an interest in the field. Gen Z isn’t flocking to the industry either, preferring jobs where they can shape company culture and have a social impact. They want to be recruiters or marketing or social media managers. For more context, the ISACA State of Cybersecurity surveyed cyber professionals, and only around 12% were 34 or younger.
Apparently, cybersecurity careers aren’t attractive to those entering the job market. Maybe cybersecurity needs a “makeover” to highlight the positives of being in demand, such as providing competitive wages and offering opportunities for advancement.
The key issue with generating interest in the industry is that these new candidates will come to the table unprepared. It could cause more “paper tigers” to infiltrate the ecosystem. Paper tigers are a rampant problem in cybersecurity. People look “great on paper” because they have this credential or that certification.
In reality, they usually don’t have the technical or people skills to be a good hire and an effective cyber professional. In fact, 55% of survey respondents stated they don’t believe applicants are well qualified, citing a lack of hands-on experience as the main factor in the unqualified classification.
In looking at specific skills lacking, the results indicated a gap in people skills as the greatest concern, followed by technical attributes of cloud computing, security controls, and coding.
So, how do we close the skills gap?
Closing the Skills Gap
The skills gap includes both soft and technical skills. As noted, people do not need one more certification or a college degree. Instead, they need practicality and real-world exposure to meet the technical requirements and support to develop interpersonal skills. For this to happen, the industry must shift how it recruits and trains.
The current tests focus on theory, not practice. It’s become easy to earn this “badge” through multiple-choice exams that anyone can memorize. Some certifying organizations still do things right, including CompTIA and EC-Council. Their programs are more practical.
The transformation that needs to occur in the talent pipeline has to be a movement that the entire industry supports. First, the field must showcase that it is one with job security, growth, and opportunity. Second, the training landscape must become consistent, teaching real-world technical and people skills. Third, employers could then make smarter hiring decisions not based on desperation.
In addition to challenges with new talent, organizations are also struggling with turnover, which is costly and disruptive. You have more control over this variable.
The Retention Problem: Is It Your Culture?
In the ISC study, 21% of respondents changed companies in the last 12 months, an increase of 13%. Digging into why, it appears to be about the culture, not the work itself. Cybersecurity can be high-stress, but many in the field enjoy what they do. The ISACA study revealed that 60% of companies had a cybersecurity retention problem, and 63% said they had open roles.
The nemesis of cybersecurity retention is the environment. You have the ability to change that if you recognize the shortcomings.
Cybersecurity culture is often toxic. People often struggle to be open communicators. They can be uncooperative and aggressive. They act this way because they know they can, and when someone new shows up, they’re not unlike a group of mean girls. Such a situation isn’t sustainable, and it only increases risk. If you want to retain the qualified people you have, you must start by laying a foundation for an inclusive, honest, and respectful culture. In most circumstances, you need to help these people evolve with better people skills.
Not everyone will want to grow and change. It’s hard, after all, and uncomfortable. Even if it’s the best technical employee you have, you may be better off without them. Those left get a choice to go through the process. There’s already a blueprint for you on how to do that with the Secure Methodology™. It’s a seven-step guide to help cybersecurity leaders support employees in becoming better communicators, collaborators, and teammates.
The Secure Methodology™ applies to employees, new and senior.
Applying the Secure Methodology™ for Recruitment and Retention
We’ve established that the work isn’t the reason why people leave. We also know there are deficits in skills and that cultures can be toxic. This is the reality that inspired me to develop the Secure Methodology™. Here’s how each step can apply to the cybersecurity workforce challenges.
Awareness
Awareness applies to one’s self and others. It’s lacking in many technical folks, which causes their actions and behaviors to be abrasive or curt. There’s an energy to it, and when people aren’t aware, it causes conflict and animosity. Through exercises and direction, your team can become more aware of themselves and others. It can be a significant shift that gives them perspective.
Mindset
You want to help people move from a fixed to a growth mindset. Only in the latter can they evolve and improve. You also have to believe that change is possible. Additionally, there must be a commitment from people to welcome growth. One activity to support this is the 7 Levels Deep exercise, which can help people understand motivations and why they do the things they do. This knowledge can unlock a fixed mindset.
Acknowledgment
To acknowledge is to express appreciation, and it doesn’t happen enough in cybersecurity. So, first, leaders should begin to do this consistently. It builds trust and confidence. An organization also must accept that a cyber professional isn’t an expert in every technical area and shouldn’t put such extreme burdens on a single person or team. It requires a culture shift that recognizes growth and contributions while ensuring accountability.
Communication
Communication is the foundation for all soft skills and really every step in the Secure Methodology™. When communication is poor, nonexistent, or comprised of technical mumbo-jumbo, breakdowns happen in your risk posture and culture. Communication is also about listening to understand, not just responding. Developing these skills in your staff will pay big dividends for them and your organization. If communication is transparent, honest, and constant, the culture moves further and further from toxicity. Within this step, you’ll find exercises and best practices for cultivating communicators.
Monotasking
Monotasking is about dedicated attention to one task at a time. It’s likely at odds with current performance, where multitasking is the norm. Multitasking is bad for cybersecurity, as it can cause excess stress and errors. Monotasking isn’t always an option, but you’ll want to ensure that your employees know it helps them focus and be more productive.
Empathy
In the Secure Methodology™, I focus on cognitive empathy, which is understanding another’s feelings and perspectives. Empathy also means choosing to connect with someone and accept their views. In such a culture, empathy builds trust, and it all goes back to communication and how people interact. If your team builds empathy, you have an environment where people want to stay.
Kaizen
Kaizen is a Japanese term that translates to “continuous improvement.” So, this step isn’t the final one. It continues as part of the foundation of culture. The pursuit of continuous improvement applies to soft and technical skills. It also supports adaptability and flexibility — traits useful to anyone, anywhere. It keeps people engaged, and that supports recruitment and retention.
The cybersecurity workforce landscape needs some care. Many areas need to evolve, and you can be a voice for that in the industry and your organization using the Secure Methodology™.
Learn more about the Secure Methodology™ by reading my book, The Smartest Person in the Room, and viewing the online course on the guide.
 The field of cybersecurity is growing, but the pool of qualified candidates is not. Nearly every industry deals with labor shortage challenges due to the pandemic, the Great Resignation, and other factors. However, cybersecurity was already experiencing recruitment and retention problems. Even with new people entering the market, it would be remiss to count them all as ready for the cybersecurity war. So, how do you recruit and hire cybersecurity professionals in these times? And is technical prowess the only factor to consider?
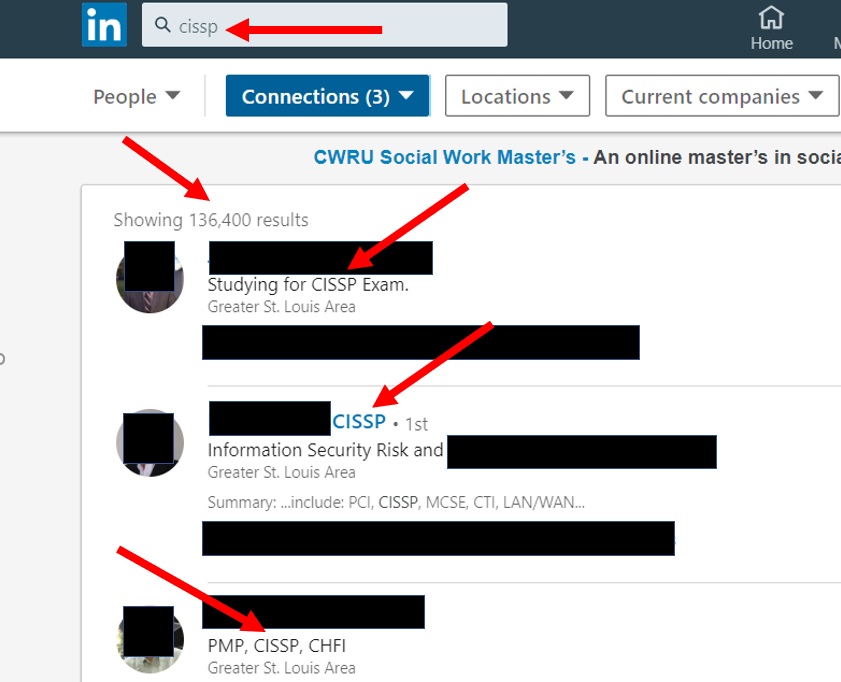
The field of cybersecurity is growing, but the pool of qualified candidates is not. Nearly every industry deals with labor shortage challenges due to the pandemic, the Great Resignation, and other factors. However, cybersecurity was already experiencing recruitment and retention problems. Even with new people entering the market, it would be remiss to count them all as ready for the cybersecurity war. So, how do you recruit and hire cybersecurity professionals in these times? And is technical prowess the only factor to consider? There are many ways to land a job that requires the CISSP (Certified Information Systems Security Professional) or any other cybersecurity certification. In this post, I share three methods to empower you to find your ideal job, leveraging your CISSP (or any other) certification. I hope these techniques enable you to land a job in cybersecurity that resonates with you.
There are many ways to land a job that requires the CISSP (Certified Information Systems Security Professional) or any other cybersecurity certification. In this post, I share three methods to empower you to find your ideal job, leveraging your CISSP (or any other) certification. I hope these techniques enable you to land a job in cybersecurity that resonates with you.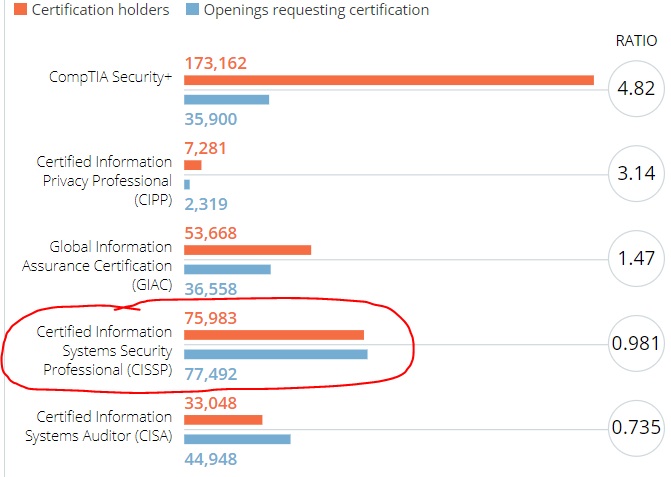
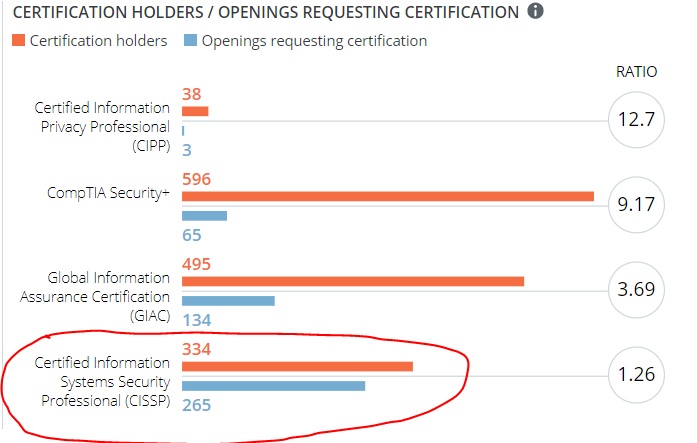
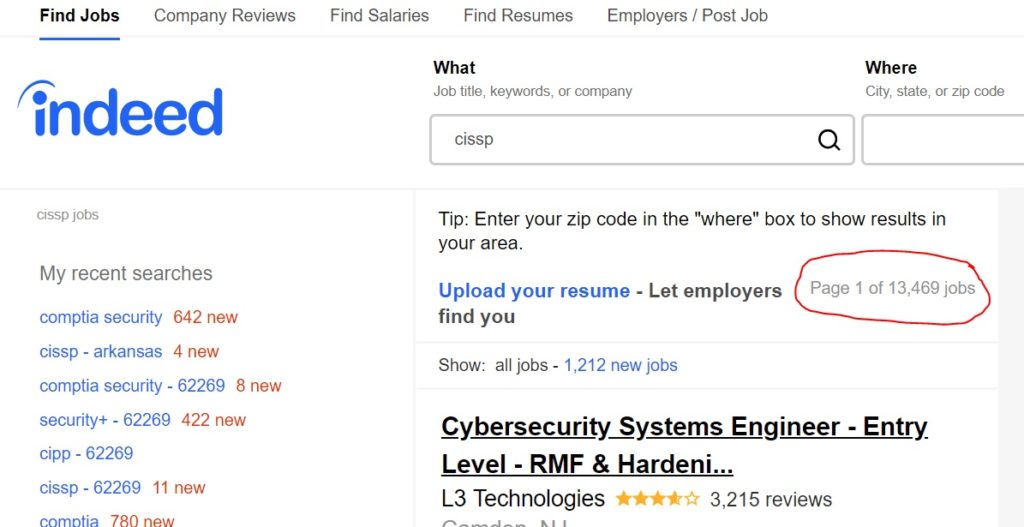
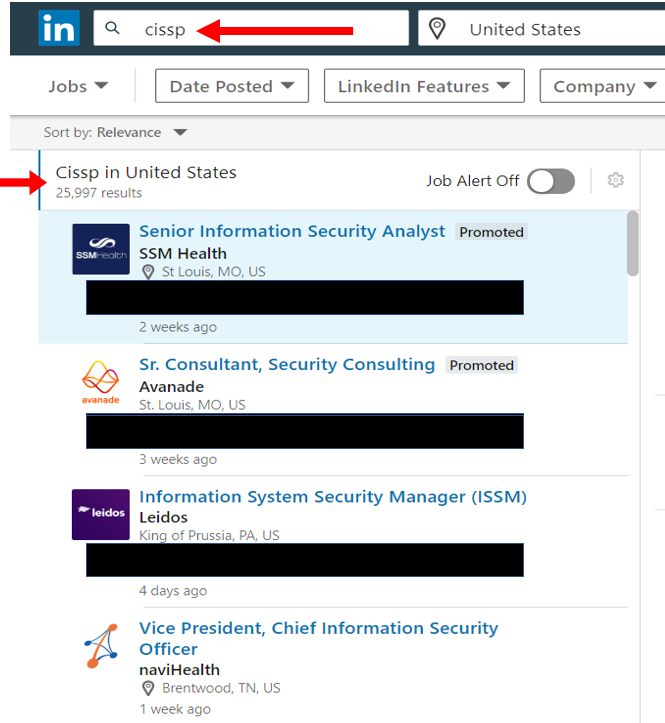
 According to the Information Systems Security Association (ISSA), we’re facing a cybersecurity skills crisis. Their
According to the Information Systems Security Association (ISSA), we’re facing a cybersecurity skills crisis. Their 




